Please refer to Class 10 Information Technology Sample Paper Term 2 With Solutions Set C provided below. The Sample Papers for Class 10 Information Technology have been prepared based on the latest pattern issued by CBSE. Students should practice these guess papers for class 10 Information Technology to gain more practice and get better marks in examinations. The Term 2 Sample Papers for Information Technology Standard 10 will help you to understand the type of questions which can be asked in upcoming examinations.
Term 2 Sample Paper for Class 10 Information Technology With Solutions Set C
1. Direction Read the following passage and answer the questions that follows Consider the following SQL command to create a table:
CREATE TABLE MEMBER
( MEM_IDINTEGER NOT NULL,
NAME CHAR(15) NOT NULL,
DATE_JOIN DATE,
ADDRESS VARCHAR(100) NOT NULL,
PH_NO CHAR(15),
);
(i) NOT NULL ensures that
(a) Column cannot have blank value
(b) Column will not accept any value
(c) Column has a fixed value
(d) Column has a unique value
Answer
A
(ii) By default format of date entered is
(a) DD-MM-YY
(b) MM-DD-YY
(c) YYY-MM-DD
(d) DD-MM-YYYY
Answer
C
(iii) The ……… constraint ensures that the value entered specifies a certain condition.
(a) NOT NULL
(b) NULL
(c) CHECK
(d) All of these
Answer
C
(iv) PRIMARY KEY in above example ensures that
(a) MEM_ID is entered primarily
(b) MEM_ ID will hold a uniquely identified value
(c) MEM_ ID will not remain blank
(d) All of these
Answer
B
(v) Which SQL command is used to create a table?
(a) ALTER
(b) INSERT
(c) UPDATE
(d) CREATE
Answer
D
2. State any three rules and netiquettes while chatting.
Ans. Any three rules and netiquettes while chatting are as follows
(i) Do Not Use All Caps Typing your message in UPPERCASE is like shouting on the Internet and very aggressive.
(ii) Give People Time to Respond Be polite while online. If you are chatting with your friend, do not ask multiple questions in a short time, so that the recipient has time to respond.
(iii) Respect Others while Chatting Give the person you are communicating with your undivided attention.
Or
How does water and foam, and carbon dioxide work to extinguish fire?
Ans. Water and foam fire extinguishers extinguish the fire by taking the heat element away from the fire. Water extinguishers are for class A fires only – they should not be used on class B or C fires.
Carbon dioxide fire extinguishers extinguish fire by taking away the oxygen element of the fire triangle and also be removing the heat with a very cold discharge.
Carbon dioxide can be used on Class B and C fires. They are usually ineffective on Class A fires.
3. Explain the three types of switching techniques.
Ans. Switching is basically of three types which are as follows
(i) Circuit Switching In this type of technique, an end-to-end path is created before sending the data (dedicated channel, i.e. Circuit). The data is transferred using physical connection which is set up between sender and receiver.
(ii) Message Switching Message switching is based on the transfer of block of messages from sender to receiver. Firstly, the address of destination is attached in a message. When a sender has a block of data to be sent, it is stored in the first switching station and then forwarded later. Each block of message is received entirely, checked for errors and then retransmitted. There is no need for any physical connection between the source and destination.
(iii) Packet Switching In this type of switching, a message is broken into packets of fixed size. Each packet has header that contains source and destination addresses information, acknowledgement and error bits.
Or
Explain any one accident that may happen in workplace.
Ans. Any one accident that may happen in workplace is as follow
Slips, trips and falls One of the common accidents in workplace is slipping on wet floor or you likely encountered slippery tiled surfaces. Other risks are falling from height while working, falling from stairs and scaffolding. These accidents can happen in any work environment and the injuries sustained can range in severity. If a person were injured in the course of work as the result of a slip and fall or other type of accident, he/she may be entitled to financial support in the form of workers’ compensation or Social Security disability.
4. What is DML and DCL?
Ans. Data Manipulation Language (DML) are the SQL commands are used for storing, retrieving, modifying, and deleting data. These commands are SELECT, INSERT, UPDATE, and DELETE. A Data Manipulation Language (DML) is a family of syntax elements similar to a computer programming language used for selecting, inserting, deleting and updating data in a database. Performing read-only queries of data is sometimes also considered a component of DML.
Data Control Language (DCL) is used to create roles, permissions, and referential integrity as well it is used to control access to the database by securing it. These SQL commands are used for providing security to database objects. These commands are GRANT and REVOKE.
5. What are the best practices to be followed for internet security?
Ans. The best practices to be followed for Internet security are as follows
(i) Do Not Share Personal Information Never share your personal information while filling online forms.
(ii) Secure Transactions Be careful while doing transactions on the Internet. Your account details, credit card number or online banking personal information can be tracked and used by unauthorised users known as hackers. Make sure, the website is legitimate.
(iii) Install Firewalls Firewall acts as a bridge between your computer and other systems from which you are getting data.
(iv) Never Install Software from Unknown Sources Verify the source or website while downloading any product or software.
Or
Define the terms network layout and topology. Explain any three network topologies.
Ans. The arrangement of connected nodes (Computers) in a communicating network is called Network Layout. Topology refers to the way in which a network is laid out physically. It is the geometric representation of the relationship of all the nodes to one another.
Any three network topologies are as follows:
Star Topology: In a star topology, each computer is connected to a centrally located device called hub. Bus Topology: In a bus topology, one long cable acts as a backbone to link all the computers in a network.
Ring Topology: In a ring topology, each computer is connected with the two computers on either side of it.
6. Damini is a programmer in an institute and is asked to handle the records containing information of students.
Suggest any 5 fields name and their data type of students database.
Ans.
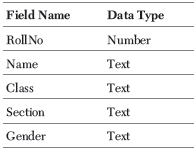
Or
Write a SQL command to create the table BANK whose structure is given below.
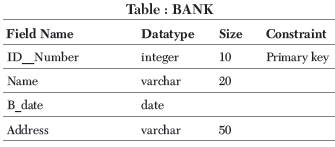
Ans. The SQL command to create a table as per given structure is as follows
Mysql> CREATE TABLE BANK (ID__Number integer (10) PRIMARY KEY, Name varchar (20), B__date Date, Address varchar (50));
7. Explain the functions of an entrepreneur.
Ans. The functions of an entrepreneur are as follows
(i) Innovation It includes introducing new products, opening new markets, new sources of raw material, and new organisation structure.
To arrange for factors of production and establishing coordination, i.e., land, labour, capital etc. in appropriate proportion and to maximise output by best utilisation of these factors after coordinating them.
(ii) Finding Suitable Market He has to search for suitable market to sell the product, for which he performs various functions advertisement and publicity, appointment of selling agents, providing incentives to various selling intermediaries to promote sales.
(iii) New Inventions Encouraging new inventions and introducing innovations in production, production techniques, sales, marketing, advertisement etc.
(iv) Establishing Relations with Government To establish relations with government and its functionaries. In this regards his functions are obtaining licences, payment of taxes, selling the product to government and provision for export-import etc.
Or
Explain the advantages of choosing entrepreneurship as a career option.
Ans. The advantages of choosing entrepreneurship as a career option are as follows
(i) Independence An entrepreneur is his own boss. He can take all decisions himself. He need not obey someone.
(ii) Ambition-Fulfilment Some people want to convert their original ideas into a new product or service. For example, smart phone, electric vehicle, driver less train, etc.
(iii) Excitement Entrepreneurship involves adventure. Some people resign their well paid jobs and launch their own venture due to excitement.
(iv) Freedom Entrepreneurship allows the freedom to try out one’s ideas. Freedom seeking people choose entrepreneurship as a career.
(v) Wealth Creation Successful entrepreneurs create enormous wealth for themselves and their staff.
8. Explain the features of database.
Ans. The features of database are as follows
(i) Datebase Management Software is Self Describing in Nature All database software have a system catalog which stores description of database objects such as tables, views, synonyms, valueranges, indexes, user groups or users etc. This description about the data itself is called the metadata or data about data.
(ii) Program-data insulation or program-data independence This feature allows us to change the structure of a database without affecting the DBMS programs that access data from the database.
(iii) Data abstraction Database management systems hide complex data-structures and irrelevant details from the users. This simplifies the view of the data and makes it easier for the users to work on the database. This approach of database design is called data abstraction.
(iv) Support multiple views of the data The database software allows each user to have their own view of the database which describes only the data that is of interest to that user or group of users.
(v) Backup and recovery facilities Backup and recovery methods of database software allow users to protect data from any accidental loss. If a computer system fails in the middle of a complex update process, the recovery subsystem is responsible for making sure that the database is restored to its original state.
Or
What is database, relational database and RDBMS?
Ans. A database is an integrated collection of logically related records or tables. A database consolidates records previously stored in separate files into a common pool of data records that provides data for many applications. The data is managed by software called database management systems (DBMS). The data stored in a database is independent of the application programs using it and of the types of secondary storage devices on which it is stored.
A relational database is a type of database where data is stored in one or more related tables, which makes it much simpler to query the database. Each table has a set of fields, which define the nature of the data stored in the table. A record is one instance of a set of fields in a table. To visualize this, think of the records as the rows of the table and the fields as the columns of the table.
The Relational Database Management System (RDBMS) is a type of Database Management System (DBMS) that allows us to create and work with the relational databases. Most RDBMS use SQL (Structured Query Language) as database query language. LibreOffice Base, Microsoft Access, and OpenOffice Base, Oracle, MySQL are examples of some popular Relational Database Management Systems.

